Firewall [A Beginner’s Guide]
Introduction
Every year many cyber attacks happen to our IT infrastructure by hacker’s. These people have one motto that is to turn down the system, ask for ransom, sabotage the image of an organization and many more. This is our responsibility to keep ourselves ready for any such incidence and keep our country safe from any such activity. Therefore, to keep our younger generation abreast with the technological advancements so I had started this initiative.
In this article, I will discuss about the basics of firewall and in subsequent articles I will discuss about implementation of firewall and use of its different features.
A firewall is a first line of defence from outsiders in a network. They can be both software and hardware. This software helps our network from any danger which might sabotage our system. Technically, it is a protective system that secures a network by filtering incoming and outgoing traffic. We can do this by defining custom rules in firewall.
There are majorly eight types of firewalls:
- Packet-filtering firewall
- Circuit-level firewall
- Stateful inspection firewall
- Application-level firewall
- Next-gen firewall
- Software firewall
- Hardware firewall
- Cloud firewall
The primary purpose of the firewall is to block threatening traffic from entering our local private network.
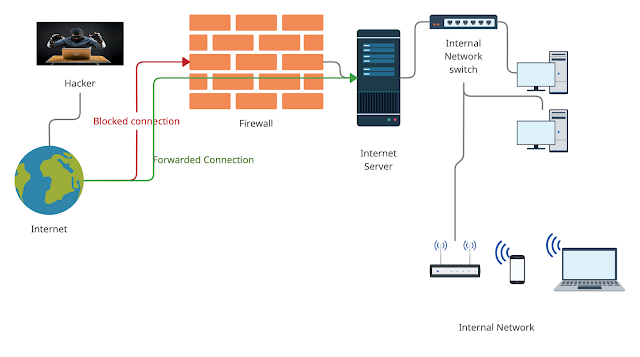
As described in Figure 1 the legitimate connection is forwarded and threatening connection is blocked.
Working
Working of a firewall depends upon opening and closing of ports or blocking and unblocking of applications running on the system. It depends on system administrator of the machine to identify whether a particular application or port should be blocked to allowed to interact with the outside world as shown in Figure 2.
The linux kernel in Ubuntu has a packet filtering system called netfilter and iptables are the suite of commands to configure it. Since configuring them is a daunting task therefore theres are many alternatives for this and one of the alternative is ufw(uncomplicated firewall). This is a frontend used for iptables. We will be discussing in our subsequent articles about these technologies and installation, configuration and deployment of Pfsense (Firewall with a web based frontend).
Firewalls basically block ports which are not required for communication by the system. It generally uses three simple commands – drop, reject and accept/allow traffic.
Let us understand these commands:
- Drop – The packets which are coming inside the system or leave are blocked directly.
- Reject – This is same as drop but the sender of the data will receive an error message about the rejection of the packet by firewall.
- Accept / allow – The packets will passthrough firewall.
These three commands are already defined within the firewall as a default policy. By using simple commands like:
To activate the firewall in Ubuntu we use following commands, on command line:
$ sudo ufw enable
To apply default rule on incoming and outgoing traffic:
$ sudo ufw default deny incoming
$ sudo ufw default allow outgoing
To open port 80 for apache to work seamlessly on internet or in other words, open HTTP traffic coming inside webserver:
$ sudo ufw allow http or $ sudo ufw allow 80
By allowing the traffic on port 80 means that traffic is allowed to come inside the server from internet and access service running on webserver. If you want to block the incoming traffic on port 80 then follow this command.
$ sudo ufw deny http or $ sudo ufw deny 80
I hope you have understood the working of firewall. In my next article I will demonstrate installation of Ubuntu on Windows machine and running firewall commands on it. If you like to article then do share it on internet. In my subsequent articles I will explain installation of web based frontend firewall, its installation and configuration. Until then happy reading and keep yourself safe from Wuhan Virus.


Comments
Post a Comment